Zoombombing: It’s Not about Zombie Bombs but Still Alarming
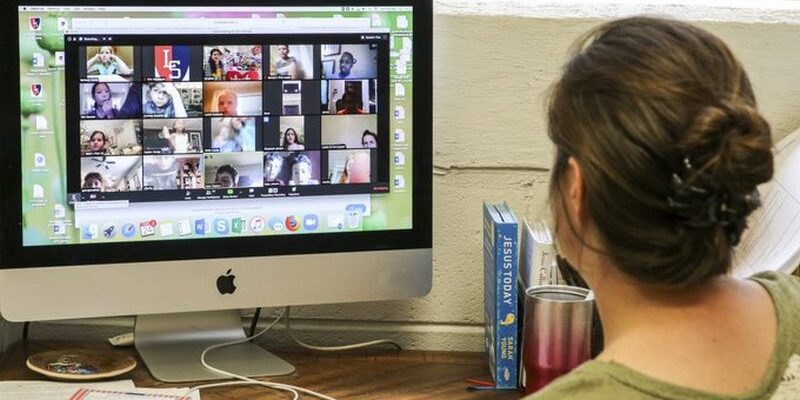
For those unaware, there’s a communication platform called Zoom, which allows people to connect through voice calls, instant messages, video calls, and content sharing. Designed to be a “people-centric” cloud service, it facilitates video conferencing, webinars, and collaboration. Zoom made it to the news recently because of a growing scheme of malicious users who share offensive videos, from outrageous pornography to repulsive violence.
What Exactly Is Zoombombing?
Zoombombing has nothing to do with the ongoing pandemic—thankfully—so there are no zombies and drastic measures like bombings to talk about here. It’s a form of trolling activity centered on the communication app Zoom.
Zoom has become increasingly popular as COVID-19 forces everyone to practice physical distancing and work from home. The platform helps people counter the lack of social interaction in the midst of quarantines and lockdowns by enabling video calls with multiple participants. Unfortunately, it has become the target of malicious internet users who exploit the platform’s screen sharing feature to vex or harass people.
One of the most prominent cases of zoombombing happened on the regular Zoom discussion “WFH Happy Hour,” which is hosted by noted investor Hunter Walk and The Verge reporter Casey Newton. A troll managed to bombard the Zoom call with disturbing content. Participants were shocked to see on the screen a clip of the infamous “Two Girls, One Cup” and other horrifyingly explicit videos.

The hosts were quick to address the incident, but the attackers easily re-entered the Zoom call using a new name and proceeded to share more appalling videos. The hosts were left with no choice but to stop the call to stop the unwanted visuals from offending the audience.
Vulnerabilities Exploited
Zoombombing is made possible by Zoom’s policy of not providing call hosts a privacy-centric default setting. Any participant in a Zoom call can share whatever they want without requiring the permission of the host.
Hosts have the option to disable this screen sharing feature by going to the Settings then the Share Screen option, then the Advanced Sharing Settings. The host should switch it to “Host Only” if they don’t want trolls or individuals who don’t have better things to do in life other than spreading mischief. Those who intend to publicly share links to their Zoom must see to it that they allow only the host to share their screens.
The zoombombing incident experienced by WFH Happy Hour is essentially a simple lesson on how it’s important to review privacy settings before using any communication platform or any app in general.
More Tips on Securing Zoom Calls
Aside from changing the default screen sharing setting, it also helps to do the following to ensure the security of Zoom calls.
- Disabling “Join Before Host” – Dong this ensures that only the expected participants are in the call before the host enters.
- Deactivating the “File Transfer” function – This is important to prevent anyone from sharing malware embedded in files.
- Enabling “Co-Host” – This is a moderation feature that allows the host to enlist other participants of a call to moderate the session. Having more moderators means faster response to problems.
- Deactivating the “Allow Removed Participants to Rejoin” – This is effectively a temporary user ban feature. It prevents call participants who have been booted from slipping in again even when using a different username.
FBI Warning
The FBI has already released a warning on the zoombombing trend, saying that it is being used to project racist and hateful imagery. Malicious users are hijacking Zoom sessions with schools, universities, and advocacy organizations as the primary targets.
Zoombombing cases have been reported from different settings. There’s one in Massachusetts wherein a teacher’s virtual classroom is hijacked by someone to display swastika tattoos. Another one in Long Beach, California has a student defending his graduation dissertation disrupted by lewd drawings and racist words scribbled on the screen. In Princeton University, a Zoom-based class was interrupted by the image of someone with his genitalia bulging on his underwear.
So far, the incidents have been limited to mischievious to offensive images. The attacks are mostly nuisances; there have been no evidence of data theft, malware installation, and other more serious cyber threats. However, authorities are warning Zoom users to be more cautious. It’s advisable to check the default privacy settings to avoid besetting or awkward incidents.