Vault 7: Wikileaks reveals CIA abusing undisclosed vulnerabilities
Image Source: Heavyeditorial
Wikileaks, an international non-profit organisation that publishes secret information, news leaks, and classified media from anonymous sources, has just published what might be the greatest leak of all time. On Tuesday, 7 March 2017, WikiLeaks begins its new series of leaks on the U.S. Central Intelligence Agency. Code-named “Vault 7” by WikiLeaks, they claim that it is “the largest ever publication of confidential documents on the agency.”
The first part, titled Year Zero, it “comprises 8,761 documents and files from an isolated, high-security network situated inside the CIA’s Center for Cyber Intelligence in Langley, Virgina.”
The story claims that recently, the CIA, who has covertly building up their own army of hackers over the years, while using and gathering undisclosed weaponized technological vulnerabilities, known as “zero days”, has recently “lost control” of their zero day arsenal, compromised and sent to a number of people, one of which is Wikileak’s source. These arsenals including malware, viruses, trojans, weaponized “zero day” exploits, malware remote control systems and associated documentation. Wikileaks claimed that the possessor of this collection of hacking tools gives that person the full capabilities of CIA’s hacking division.
These powers include the ability to hack into any products from leading tech companies, like Google’s Android, Apple’s iOS, Microsoft’s Windows and Samsung’s TVs, turning them into instant microphones and cameras for the CIA. Another example the ability to hack into phones via WiFi, gathering all the data from all the phones connected to that WiFi signal.
One of the reasons seen as to why would CIA needs such vast cyber weaponry is because of their rivalry with the US’ National Security Agency, who has their own hacking arsenal. They usually have to disclose their operations to the NSA in order to gain NSA’s hacking capabilities. But on 2001, the CIA has gained political and budgetary preeminence over the NSA and started to build their own army of hackers so they don’t have to tell anything to the NSA.
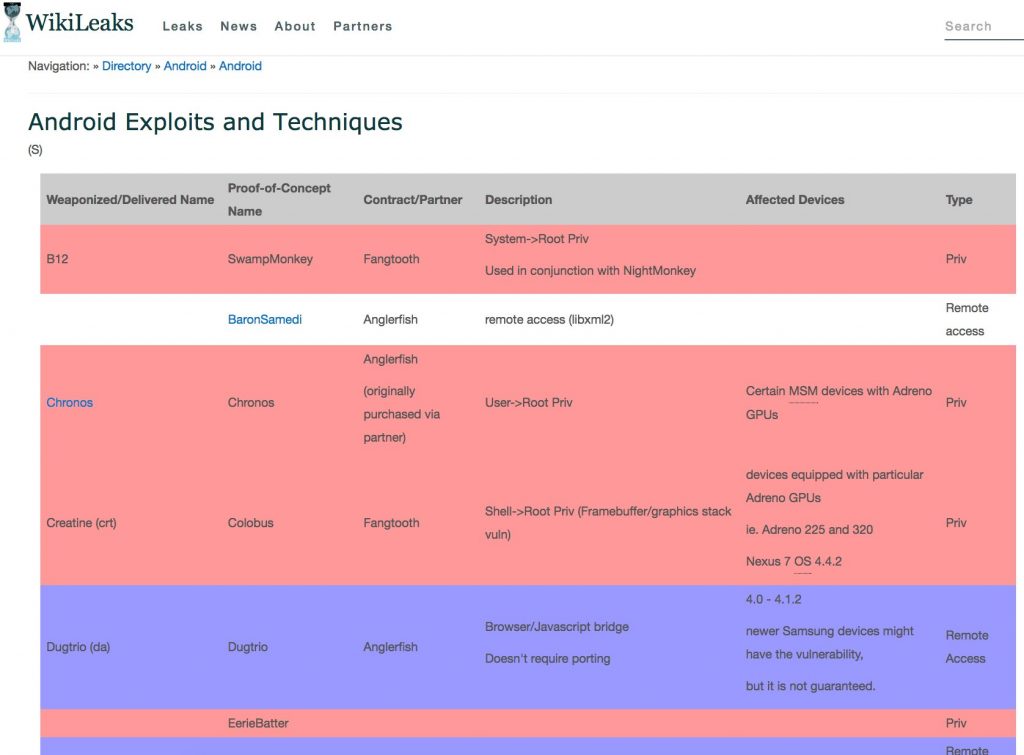
Image source: Wikileaks
Wikileaks claimed that by the end of 2016, the CIA’s hacking division, formally known as the Center for Cyber Intelligence (CCI), had over 5000 registered users and had produced more than a thousand hacking systems, trojans, viruses, and other “weaponized” malware.
According to the Vault 7 leaks, the CIA’s Engineering Development Group are the ones responsible for creating the malware and hacking tools they use, one of which is known as “Weeping Angel”, developed by CIA’s Embedded Devices Branch, infects smart TVs to turn them into microphones. To the victim, his smart TV looked like its turned off. But in reality, the Weeping Angel has put it into a kind of fake “off-mode”: its actually on and is recording everything it can hear, sending it back to the hacker.
Another part of the leak has put CIA into a list of possible suspects of a gruesome murder. Michael Hastings, a reporter for Rolling Stone, was investigating then-CIA Director John Brennan. Earlier in his career, his investigation and report has led to the removal of General Stanley McChrystal from his post as ranking US commanding officer in Afghanistan. Michael died in a car crash on June 2013. Former U.S. National Coordinator for Security, Infrastructure Protection, and Counter-terrorism Richard A. Clarke said that what is known about the crash is “consistent with a car cyber attack”. He said “There is reason to believe that intelligence agencies for major powers — including the United States — know how to remotely seize control of a car. So if there were a cyber attack on the car — and I’m not saying there was, I think whoever did it would probably get away with it.”
This puts CIA in hot waters as Wikileaks reveals that on 2014 the CIA was also looking at infecting the vehicle control systems used by modern cars and trucks. In the CIA’s list of “potential mission areas,” one of the targets listed is “vehicle systems (e.g., VSEP),” most likely referring to the embedded computer systems on modern cars.
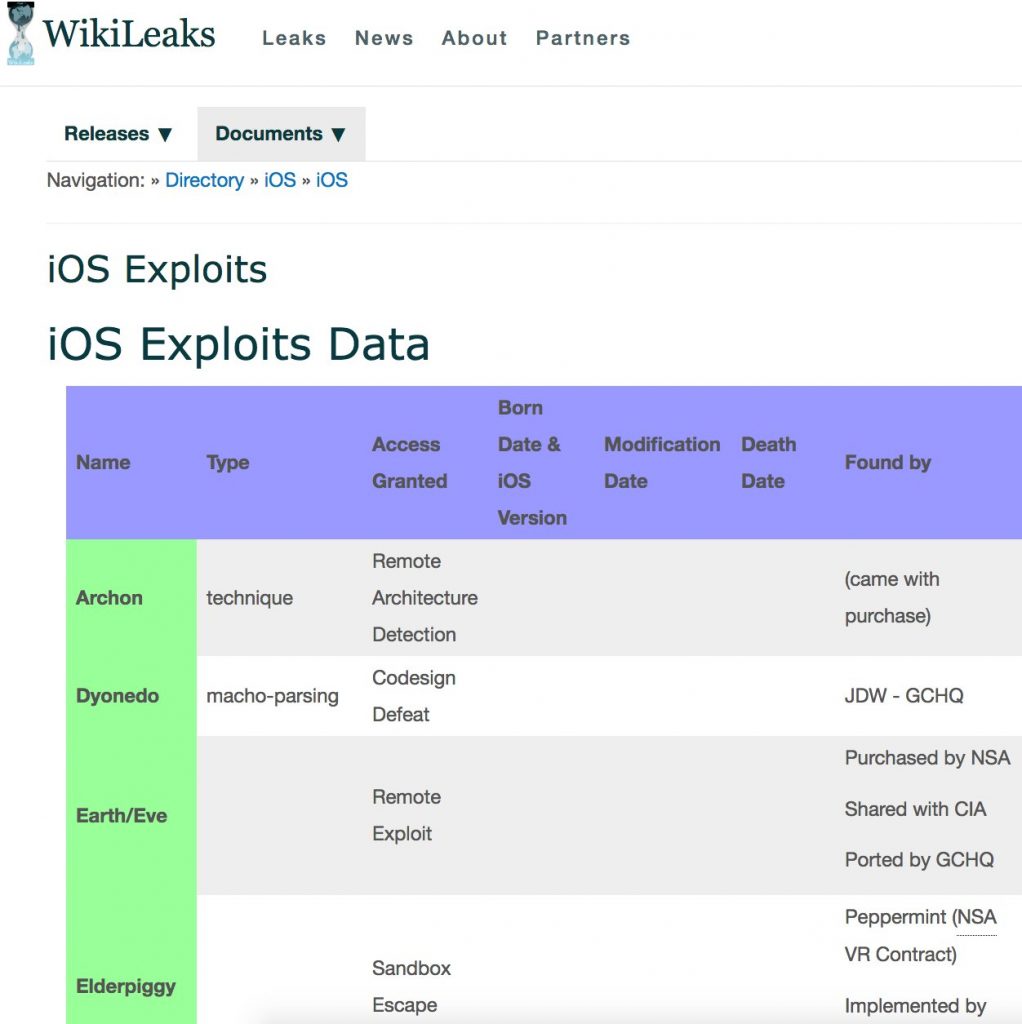
Image source: Wikileaks
The leaked alleged that CIA, to build such arsenal, has breached the Vulnerabilities Equities Process, where the US Government has pledged to disclose all pervasive vulnerabilities discovered after 2010 on an ongoing basis. Instead they kept some to themselves for their use. The leaks also said that CIA has analyzed and stole hacking techniques from rival intelligence agencies. Each hacking technique leaves a unique evidence behind and usually each intelligence agencies has several hacking techniques that can be attributed to them. CIA stole these so they can use these techniques for themselves and frame the hack to other agencies.
So far Google had not reacted to the leaks. Apple reacted to it and said that some of the vulterabilities have been fixed already. Microsoft and Samsung both said that they are “still looking into it”.