The Unwelcome Role of IoT Devices in Recent Massive Cyberattacks
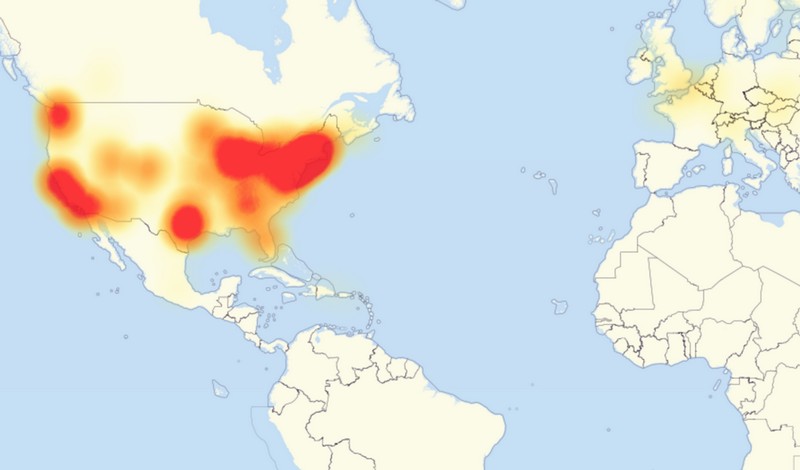
Image credit: DownDetector via Wikimedia Commons
It was not unforeseen but reality took a hard hit these past few weeks after security experts discovered that Internet of Things or IoT devices played vital roles in launcing a massive cyberattack that led to the outage of websites mainly in the US. Most of the systems affected were those located on the East coast. The outage started at around 7:00 in the morning ET on Friday, October 21, 2016, and was resolved after a little over 2 hours. A second attack took place in the afternoon, at around 4:00 PM. The problem was reportedly resolved by around 6:00 PM.
The Attacks and the Websites Affected
The unanticipated cyberattack targeted Dyn, a DNS (Domain Name System) provider based in Manchester, New Hampshire. This involved numerous DoS (Denial of Service) attacks, in tens of millions in DNS lookup requests coming from a multitude of IP addresses. The attacks were claimed by the New World Hackers and Anonymous.
As the The massive cyberattack overwhelmed Dyn’s servers, it forced several major websites to go down. These websites include Tumblr, Twitter, Reddit, Visa, Netflix, Wikia, Wix.com, Xbox Live, SoundCloud, Shopify, National Hockey League, Mashable, CNN, BBC, Business Insider, Comcast, The Guardian, The Wall Street Journal, EA, Fox News, The New York Times, PayPal, Squarespace, Spotify, Yammer, Wired, and Verizon Communications.
Image credit: Dyn (Dyn Status Updates screenshot)
The Nature of the Attack
Investigations revealed that the attacks were highly complex and incomparable to the usual DDoS attacks encountered by servers. According to Akamai Technologies, the attack involved a botnet called Mirai coordinated using a multitude of IoT devices. These devices include residential gateways, routers, DVRs, baby monitors, and web cameras. Dyn revealed that they detected a surge of malicious requests coming from millions of different IP addresses.
The Mirai malware is notable for being capable of brute-forcing its ways through the security layers of IoT devices. Mirai has in its source code more than 50 username and password combinations that are used in trying to gain access to an IoT device. Once infection succeeds, it enables remote connection. Infected devices usually continue to function normally although some may experience sluggishness. Since several IoT devices share the same settings or are allowed to operate with just default settings, they tend to be easily infected.
Mirai infection can be eliminated by simply rebooting a device or by turning it off and on again. However, the infection returns minutes after the reboot unless you quickly change the password of the device. To prevent reinfection, if you have a device you suspect of being infected, you can reboot it and quickly change its password upon startup.
The recent massive cyberattack in the US is not the first time Mirai was employed. It was used in a DDoS attack last September 2016 on the site of Krebs on Security. It was also used to attack OVH, a French web host.
Emphasizing the Involvement of IoT Devices
Why were IoT devices used? What makes them viable in launching a cyberattack? There are two highly important reasons: their number and the relative ease in infecting them.
![By Wilgengebroed on Flickr [CC-BY-2.0 (http://creativecommons.org/licenses/by/2.0)], via Wikimedia Commons](https://techtheday.com/wp-content/uploads/2014/09/Internet-of-Things.jpg)
By Wilgengebroed on Flickr [CC-BY-2.0 (http://creativecommons.org/licenses/by/2.0)], via Wikimedia Commons
Moreover, IoT devices are easy to infect. Since many users tend to not change the default passwords, these devices are not that well protected. Notably, security experts have observed that hackers are increasingly targeting IoT devices. Even for devices whose passwords have been changed, Mirai infection can still be possible because this malware spreads through telnet and SSH, which are not web-interface-based (they are command-line-based).
The problem with IoT devices now is that not many manufacturers are properly providing adequate protection for them. While there are those that have already started requiring unique passwords before they are used, majority of them are still being sold without emphasis on proper security and protection.
Lessons Learned
The recent major DDoS attacks should be a wake up call for the industry and for users of Iot devices. Manufacturers, users, and government regulatory bodies need to acknowledge the significant threat posed by inadequately protected Internet of Things devices. Fox Business has a good piece regarding this issue, highlighting the things businesses must learn from the recent Mirai attacks.
IoT devices provide great conveniences and are rapidly expanding and gaining new users. It’s only right to pay attention to the security aspects of these devices. They are meant to make lives better and not to serve as tools for enabling large scale cyberattacks.