Research: iPhone Permits Deep Personal Data Extraction
Although many would no longer be surprised by this, it’s still worth writing about the news that iPhone has been found to be permissive to deep personal data extraction. This was acknowledged by Apple employees after a forensic scientist showed how iPhones take an unexpected amount of information for “services” Apple is claiming to be for diagnostic purposes meant to help engineers.
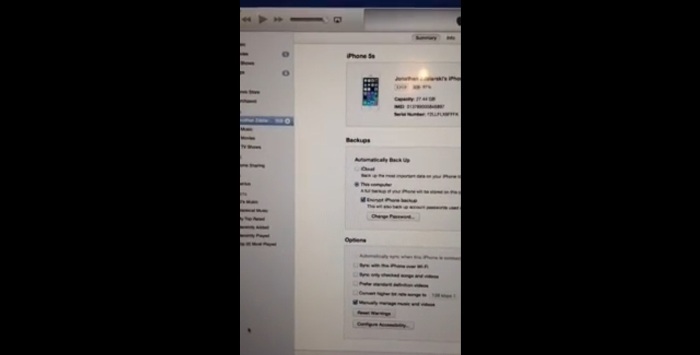
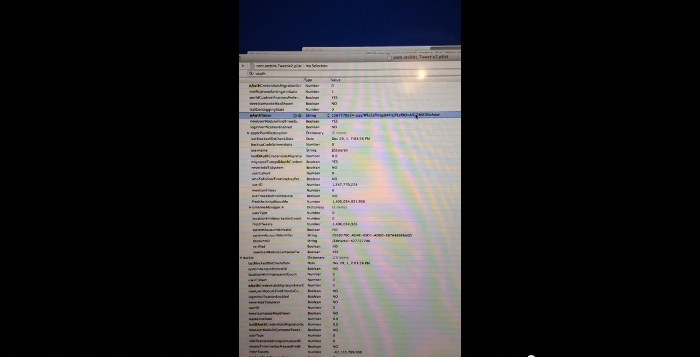
At the Hackers on Planet Earth (HOPE) conference forensic scientist and hacker Jonathan Zdziarski revealed how certain “services” run on iPhones are taking information virtually every iPhone user is unaware of. The information being taken include text messages, contacts, and even photos. The techniques involved in doing this are unknown. They are not part of what Apple has divulged to the public. These techniques are similar to the ones used to circumvent backup encryption and could be used by those who have access to “trusted” computers.
No Notifications, Unable to Disable
Zdziarski noted that these information gathering “services” don’t raise any notification to the iPhone user. Even worse, users have no way of disabling them. There is also no way of blocking future connections. Moreover, users don’t know which computers are being considered “trusted” to receive the information taken by the iPhone “services.” The “trusted” status for a computer is designated through the backup process and iPhone users are unlikely to know if a computer has already
In a video demonstration posted last Friday, July 25, Zdziarski said that “there’s no way to unpair except to wipe your phone.” In the video, he showed how it is possible to extract information from an unlocked phone through a “trusted” computer. If you click on the link to view the video, be sure to choose the higher resolutions (720p or higher) since it’s quite difficult to see the details in the awkwardly oriented video.
Collaboration with NSA?
Expectedly, many pointed out how the covert data gathering could be related to the NSA snooping. As information on Zdziarski’s findings spread, some consider it as an evidence to back claims that Apple is indeed working with the National Security Agency to undertake secret data collection from citizens not just within the United States but also in other countries. Obviously, the iPhone is also a popular device among high ranking officials in other countries so it’s not difficult imputing malice behind such covert Apple data collection practices.
Apple, however, denied providing any back door sourced information for intelligence agencies. According to a statement from the company “We have designed iOS so that its diagnostic functions do not compromise user privacy and security, but still provides needed information to enterprise IT departments, developers and Apple for troubleshooting technical issues.” The company adds that it will be necessary for an iPhone user to unlock the device and agree to trust another computer before that computer becomes a “trusted” device capable of accessing the information Zdziarski pointed out.
Overhyped Data Collection Issue?
Despite everything, Zdziarski submits that the “services” were not really aimed at spies. He notes, though, how the information obtained seem much more than what was needed and with too little disclosure. Zdziarski is calling for Apple to consider doing some modifications on the way things work with these diagnostic “services.”
Rich Mogull, a security industry analyst, agrees with Zdziarski’s assessment and says that there’s an apparent overhyping going around. Mogull thinks Zdziarski’s revelation is accurate but points out that the only way to get the information is to compromise security. For Mogull, if Apple or another party seeks to obtain the text messages, contacts, photos, and other information, users will likely know about it since the device will have to be subjected to a process to defeat its security protocols.
Apple was asked by Reuters if the company ever made use of the “tools” within iPhones to fulfill law enforcement requests. The company did not provide an immediate reply. Apple might want to cry fowl over the media’s treatment of the supposed “back doors” but considering the company’s ambiguity in answering other important questions such as the alleged NSA collaboration, the hype may not completely be that unwarranted.