Juice Jacking: The Cyber Attack that Targets Travelers
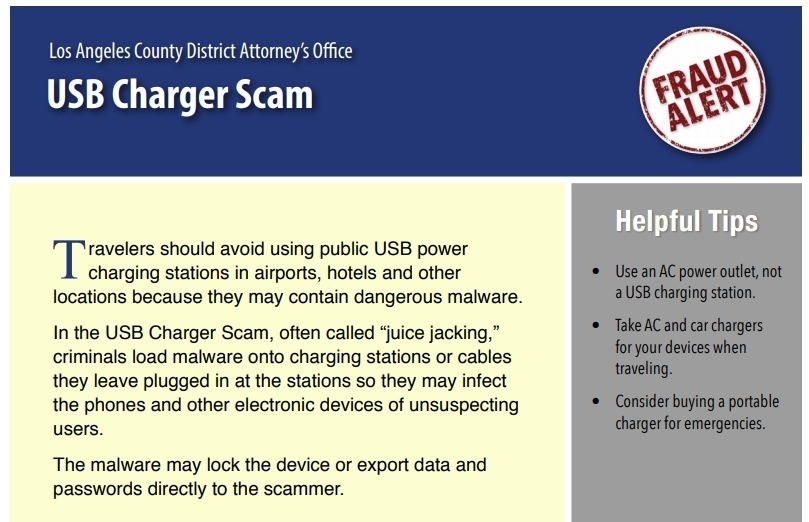
Juice jacking is not a recently devised cyber threat. It has been around since the start of the decade. However, the buzz about it is reemerging as recent reports warn about its prevalence. Of particular interest is the warning issued by Los Angeles County District, which advises travelers to avoid using public USB power charging stations in hotels, airports, and other locations because they may have harmful malware.
The Nature of Juice Jacking
Juice jacking is a form of cyber attack that targets devices that are being charged typically through their USB ports. Travelers tend to be the popular targets of this attack since many of them recklessly use charging ports offered by establishments in the different places they visit. The primary goals of this attack are to copy data from devices surreptitiously, infect the device with malware, and initiate encryption.
The data that can be stolen from smartphones, tablets, or other USB-charged devices include saved passwords in apps, contacts, banking details, and personal information. Photos, videos, and other multimedia files may also be targeted as they can be used for extortion or other similar crimes.
The malware that may be injected into the devices of unsuspecting owners are not limited to viruses. They may include adware, spyware, keyloggers, and ransomware. Most malware aim to monetize or get something beneficial from the attack. Adware are used to generate ad revenues using the unsuspecting device owners. Spyware and keyloggers try to obtain critical data such as personal information, credit card numbers, usernames, passwords, and email addresses.
Device locking or encryption, on the other hand, is a serious concern. It is usually achieved through ransomware. After a device has been locked, a message is displayed to provide instructions on unlocking or decryption, usually requiring the transfer of funds through cryptocurrency or some other anonymous means to send money. Victims need to pay the “ransom” for their smartphones or tablet computers to be decrypted. Refusing to pay often leads to the permanent inability to access of the locked or encrypted files.
File encryption attacks are unlike virus and other malware infections, which may still be remedied by sanitizing the infected file or reconstructing it into a useful copy of the original. Encrypted files can no longer be accessed sans the correct decryption code and method.

Origin of Juice Jacking
The term emerged in 2011 when Brian Kerbs, an American journalist best known for his coverage of cybercrimes, used the phrase “juice jacking” when he did a report on an informational cell phone charging kiosk put up in the Wall of Sheep at DefCon 19. This kiosk was established to raise awareness about the risks associated with the USB charging of devices in public places.
The kiosk is initially labeled as a “free charging station,” but once someone tries to use it, the label turns into a warning that tells users they “should not trust public charging stations with their devices.” This is because of the attack framework called P2P-ADB, which takes advantage of the USB On-The-Go feature to access devices.
Juice jacking went on to become a relatively known cyber threat. In September 2012, it was featured in an episode of the Hak5 hacking series. By late 2012, the US National Security Agency (NSA) published a warning to government employees who may be using public USB charging stations. The NSA required government employees to only use their personal power charging cables or bring their own power banks. In April 2015, juice jacking became the focus of an episode of CSI: Cyber.
Mitigating the Risks
Google and Apple have already implemented changes in their Android and iOS operating systems to address the juice jacking threat. In particular, they have disabled the automatic mounting of devices as hard drives whenever they are connected to a USB cable. However, it’s not enough to rely on OS-based defenses. It is advisable to exercise more caution by following these tips:
- Always bring your own charger and use AC power outlets instead of USB power ports. There is no extant technology that can access the data connections of USB cables through power lines.
- Use your own power-only charging cable if only USB power ports are available. USB cables have four tiny wires inside them. Two of them are for power (red and black), while the other two are for data (white and green). Power-only cables don’t have the white and green wires.
- Bring a power bank or buy one if you really need to charge. It’s a worthwhile purchase since you will most likely be using it frequently.
- If only a USB power port is available and you are limited to a data-and-power USB cable, charge your power bank instead of your device.
- Consider using a USB condom, a tiny device (shown below) that disables data connection when charging through a USB cable with both data and power wires

In Summary
Juice jacking is a serious risk that can affect billions of people worldwide. Coupled with social engineering, it can pierce through software-based defenses put in place. It’s only right to take the threat seriously. The preventive measures against it are indubitably easy to do, so falling prey to this kind of attack is usually the result of indolence.