The Supposedly Highly Secure Blackphone Hacked in Minutes?
Since the NSA snooping scandal erupted, privacy and security with personal devices have become quite hot topics. A number of mobile phone manufacturers have even decided to introduce new devices or features that emphasize device privacy and security. Boeing, for one, released the Black Phone, touted to be a highly secure phone designed to be safe from spying and other forms of intrusion.
There’s another smartphone also called a Blackphone which figured in the news in recent months because of its supposed high level of security and privacy protection features. It is dubbed as a 21st century smartphone that combines a custom operating system with applications optimized for security. However, this smartphone was said to be hacked in a matter of minutes at the Def Con security conference.
The Hacking
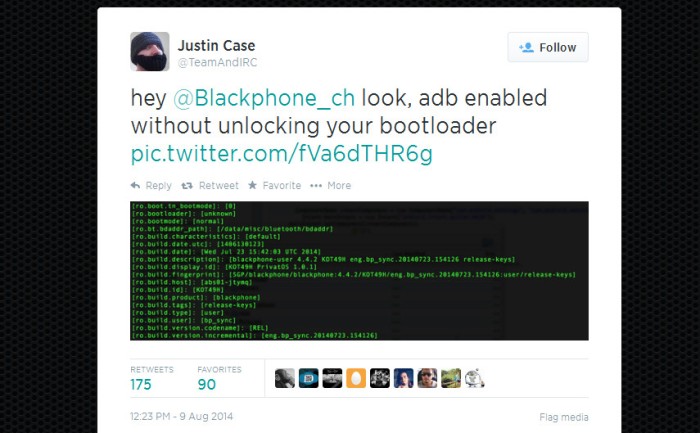
The supposed hacking was achieved by and declared by hacker Jon “Justin Case” Sawyer on Twitter also known as @TeamAndIRC. He claimed to have found three vulnerabilities and hacked the phone on three separate occasions to gain root access. He posted a message on Twitter directed to @Blackphone_ch saying “…look, adb enabled without unlocking your bootloader.”
Sawyer managed to gain root access to the Blackphone in less than five minutes. He did this by going through the Android Debugging Bridge (ADB). He achieved it even without using a bootloader. In an interview with Ars Technica, Sawyer said that rooting the Blackphone required the following conditions:
- Physical access to the Blackphone to have it connected to a computer via USB
- A Blackphone configuration that goes against what the phone is prescribed to have
- Absence of encryption
- Dismissing the Unknown Application Source warning
- Knowledge of the phone’s PIN code
These conditions are quite tough. Basically, it means that the Blackphone to be “hacked” has to be something owned by a naive user who can’t even protect his or her own PIN code.
Blackberry promoters and fans proceeded to assailing the Blackphone for the alleged breach. However, Blackberry itself is not in a position to be mocking other companies for security issues. Ironically, researchers from Accuvant found vulnerabilities in Blackberry and other smartphones, including those running iOS and Android. The vulnerability enables remote attacks on BlackBerry and other devices, making it possible to get rooted even without touching the phone.
Of note, it was a BlackBerry blogger at N4BB who drummed up the story of a Blackphone hacked. The blogger posted a story with a contentious title “Blackphone Rooted within 5 Minutes.” This post is arguably the source of most other posts that hyped the alleged quick hacking of the Blackphone.
Was There Really a Successful Hacking?
Blackphone’s makers responded to the alleged news of the hacking by downplaying it and claiming that it’s not at all a form of hacking. At the least, it’s an attack that does not account as something critical or material to cause security and privacy issues. The company claimed that getting access through ADB is not a major problem since it is just a part of the Android operating system. Blackphone uses PrivatOS, an Android based operating system.
Moreover, the Blackphone team said that ADB doesn’t really provide root access by itself. It simply gives a user full access to the device through a USB-connected computer. It is a “standard part of every Android install” according to Toby Weir-Jones, the CEO of SGP Technologies, the company responsible for Blackphone. Another defense for the Blackphone comes from Dan Ford, as he posted in a blog SGP Technologies’ stand on the supposed problem with ADB. He said that ADB was not activated in the Blackphone not because it is supposed to be a security implementation. The reason it was deactivated is a bug—a USB “boot loop” bug that emerges when the phone’s encryption is turned.
Nevertheless, SGP Technologies admitted that the vulnerability with the Blackphone’s remote wipe functionality needs to be addressed. This vulnerability poses the risk of an attacker getting elevated system privileges. The company already sent out a patch to remedy this problem in an OTA update.
Needs for Improvement SGP Technologies Willingly Admits
While the makers of the Blackphone stand by their claims of the device’s high level of security, they admit that there are still issues that need to be fixed without necessarily naming these issues. SGP Technologies is now preparing an exclusive app store for the Blackphone to be able to provide a curated collection of apps that can’t cause problems on the device. The company is trying to show resolve in ensuring Blackphone’s security and responsiveness to customer demands and requests.