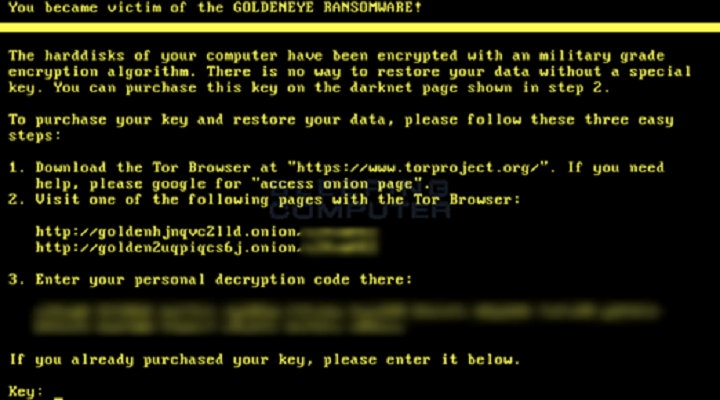
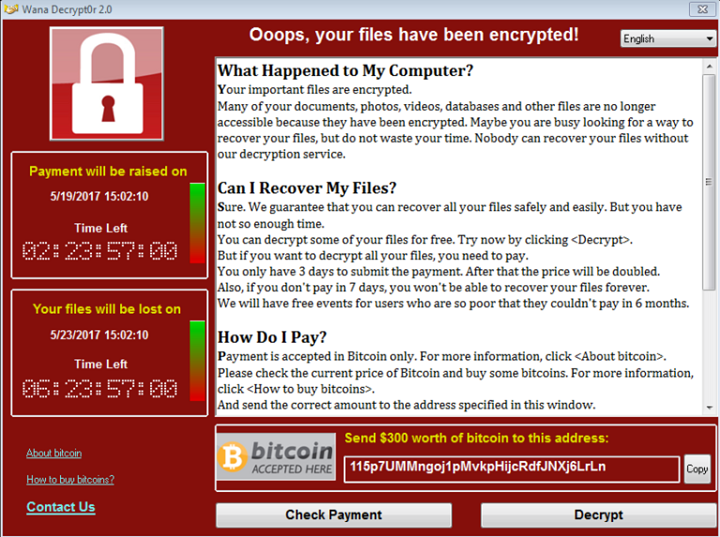
The Petya-GoldenEye Attack Said to be Possibly a State-Funded Attack
The latest ransomware attack could have been disguised as an attack made by an enemy state to blame anonymous hackers. This is what some believe after Matthieu Suiche, a hacker and founder of Comae Technologies wrote in a blogpost that the NotPetya (also known as GoldenEye) ransomware that attacked last week was in fact a “wiper.”
Wiping Your Data
A wiper, as Matthieu explained in the Comae blog, is a malware designed to destroy data. While ransomwares are designed to make money then let you retrieve the data afterwards, this malware is designed to destroy everything with no hope of recovery. It’s a relatively new type of malware, with dates of documented wiper attacks going back as far as 2012.
Wiper attacks are not common and are actually rare, and most of them are designed to attack specific files stored in specific computers in a specific nation. A good example of this is the Wiper attack in 2012 against Iranian oil companies. According to analysis, Wiper shared traits with DuQu and Stuxnet worms but it wasn’t proven if they were actually related. They also found traces of the Flame malware from the infected hardrives but no one could prove that there was a relationship between the two malwares.
Another documented wiper attack was in 2012 concerning 30,000 computers in Saudi Aramco getting wiped. The wiper concerned was called Shamoon. The Shamoon attack was claimed to by a group named “Cutting Sword of Justice”, though any detail about the group is still unclear.
Sony also had a run-in with the malware as well. In December of 2014 Sony claimed that they were attacked by North Korea. Though there was no formal name for the malware used, a Sony spokesperson describes the malware as “very sophisticated.” What’s only known is that the malware takes advantage of MS Window’s own management and network fire sharing capabilities to spread.
The Ransomware That Isn’t
Matthieu and other experts were continuing analysis after the ransomware hit last week. Apart from discovering from the code that the malware was in fact a wiper, they also uncovered more proofs that point to the whole affair being a state-funded attack against another state. One of these proofs is the fact that the email address of the attackers turned out to be a dud. The people affected won’t be able to contact the hackers if they decide to play for the locked files.
Another reason that the ransomware might be bogus is that the personal installation key that appears on the screen when the warning appears is fake. The actual installation key can be found in a README.TXT located in an affected drive after the ransomware encrypts everything, which is totally useless anyway since the email is a dud as well. Then there’s also the fact that they found the encryption process of the supposed ransomware to be buggy. Getting hit by the ransomware might cause some files to be permanently damaged and un-decryptable.
The conclusion drawn was that the ransomware was a lure to control the media narrative. They made the media believe it was another ransomware attack like WannaCry made by some faceless hacker group instead of being a state-funded attack.
“The attacker took an existing ransomware which they repackaged,” Matthieu wrote in the blogpost.
He also said that the online attacks against Ukraine have increased since the attack, and that the attackers were very subtle in their control of the media narrative by disguising this new attack as a ransomware attack.
If it is true that the latest attack is actually an attack against Ukraine, which is the country hit the most by this incident, then this is probably one of the most costly attacks ever: setting Ukraine aside, CNET reports that there have been 200,000 other computers affected around the world.