Recently Discovered Drupal, WordPress Bugs Open Websites to Cyberattacks
The very popular web publishing platform WordPress and Drupal, an open-source content management platform, have been found to be suffering from bugs that make websites and blogs vulnerable to cyberattacks. This was first reported by Nir Goldshlager, a security researcher from Salesforce.com.
The Bug
The Drupal and WordPress bugs or vulnerabilities are centered on XML Denial of Service, a risk for websites that, according to Goldshlager, is predicated on the XML Quadratic Blowup Attack. This attack poses a significant risk for websites or servers. In a blog post, Goldshlager opines that “this bug can be utilized without the aid of any plugins, and it functions smoothly on the Default installation of WordPress and Drupal.” He adds that “only one machine is needed to exploit this vulnerability.
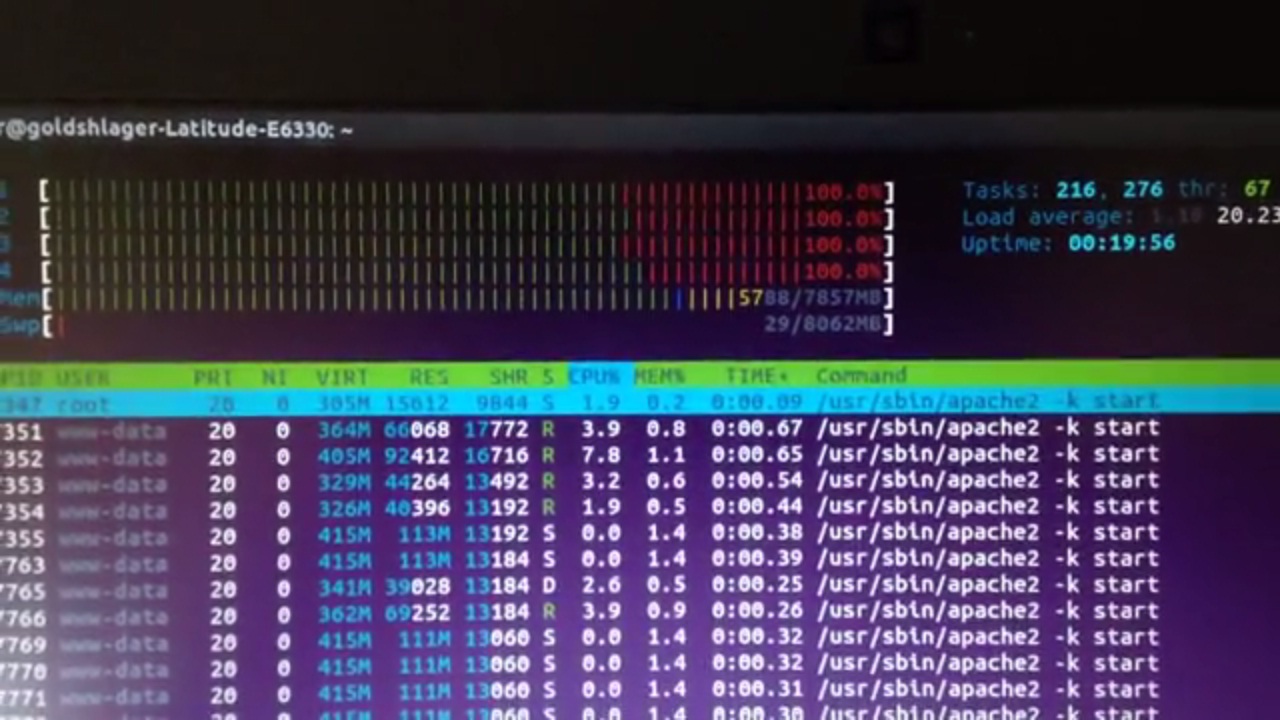
If someone decides to exploit this vulnerability, the entire central processing unit and RAM resources of a server can be consumed. This means that a website effectively becomes inaccessible. This attack is significantly different from the customary XML bomb exploitation because it adversely changes the way Memory Limit and MySQL, and Apache Max Clients works. As Goldshlager emphasized, to cause problems on sites that use WordPress and Drupal, only one machine needs to be exploited.
As of August 2013, nearly 20% of the top 10 million websites in the world use WordPress as their publishing platform. A cyberattack aimed at these WordPress created sites can lead to a major disruption on the Internet. On the other hand, there are over a million websites that use Drupal, also quite a considerable number.
Denial of Service Attack and XML Vulnerability
A Denial of Service or DoS attack is a form of cyberattack that is centered on making the resources of a machine or network inaccessible to the intended users. This attack can be undertaken in a variety of ways but the basic idea is that an attacker attempts to temporarily or indefinitely prevent a host from connecting to the Internet. It is carried out by one person or system. A Distributed Denial of Service attack, on the other hand, is undertaken by two or more persons.
XML Vulnerability, as mentioned earlier, employs an XML Quadratic Blowup Attack, something comparable to the “Billion Laughs Attack.” It enables a tiny XML document to become powerful enough to completely interfere with the operation of a server or machine in a matter of seconds. The XML Quadratic Blowup Attack uses a system called entity expansion that repetitively replicates one large entity with thousands of characters. This attack makes a small XML document with a mere 200 KB size capable of bringing down a website or server by expanding into hundreds of megabytes or several gigabytes in size.
Goldshlager prepared a video demonstration to show how the possible exploits would work on the vulnerabilities in WordPress and Drupal. He also posted screenshots to highlight the risks including the “Service Unavailable” problem that can lead to too many open connections and the manifestation of the 100% CPU and RAM usage.
Extent of the Bug
This bug is affecting versions 3.5 to 3.9 of WordPress and is already existent on default installation. With Drupal, the bug affects versions 6.x to 7.x. Again, the bug is already open for cyberattacks upon default installation.
In his blog post, Goldshlager points out that attackers can exploit the Drupal and WordPress bug by sending malicious entity requests. The requests can be sent externally and internally. At present, most websites are already adequately protected from external attacks or the malicious external request sending but with the bug present, websites and servers can be highly susceptible to internal attacks.
The Solution
Fortunately, WordPress already released an update to address the problem. WordPress version 3.9.2 is already available to counter the bug, plugging the hole in the possible Denial of Service issue in PHP’s XML processing. Nir Goldshlager actually contacted WordPress before publicizing his findings so WordPress, through Michael Adams and Andrew Nacin of the WordPress security team, already had the update ready the day after Goldshlager’s blog post about the vulnerability problem. Similarly, an update for Drupal has also been released. The update was produced by David Rothstein of the Drupal security team. Of note, this is the first time the two projects have coordinated their actions in releasing security updates to address a common problem.