Cryptominers Have Gone Rogue: Now Uses Javascript and Malwares
The crypto-currency bubble has popped and the value of these e-coins have fallen since they peaked in December last year, where Bitcoin’s price has soared to as much as $18,000 USD. The lowest since the bubble popped was on February 6 this year, at $7,700 USD. From that day onward it seems to be on the rise again with prices playing at $8,000 USD.
The sudden rise to fortune of those who are addicted to crypto-mining, is no doubt, the envy of all those who laughed at them when Bitcoin was in its infancy, starting out less than a dollar. But with the sudden rise to fame brought by cybercriminals, the price has risen so much that criminals and scammers are now taking a new approach on how to earn more of this electronic money other than spreading ransomware, from secretly running javascript via ads to using malware that infects other people’s PC. These types of techniques are nothing new. But with the rise of prices, they are gaining popularity and are now on the rise.
Cryptojacking
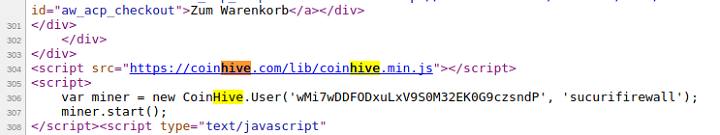
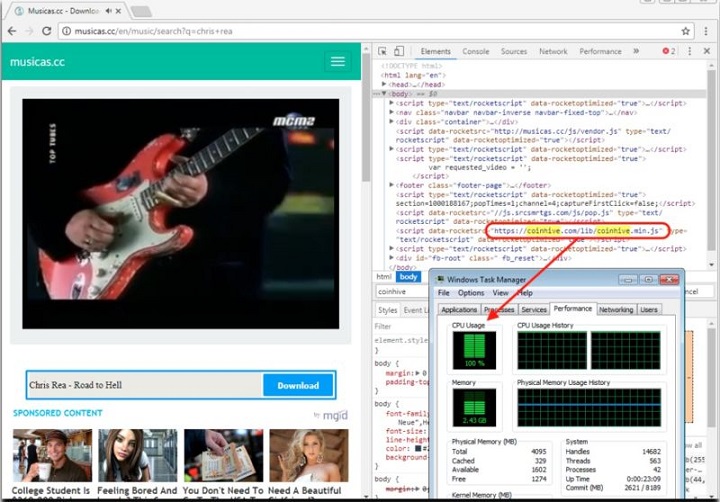
It is all thanks to cryptojacking – that is, the ability to run cryptomining software through the browser of other users – that we now have this dilemma. In November of last year, 2,496 websites have been found using cryptojacking on their sites’ visitors. Of course, the visitors of these websites were unaware of the website stealing RAM from them. This is done using the Coinhive javascript, which is a cryptominer mining the cryptocurrency Monero. They embed it into the webpage’s code, usually in the very familiar “<script>” tags.
When the miner starts running on your PC, it eats up the RAM, which could potentially slow down your computer, or increase the heat generated by your device, which could cause damage to your hardware. People are advised to have script blockers and the usual Adblock when visiting unfamiliar websites to avoid getting their PCs’ RAM used up.
Coinhive is usually treated as a separate case. However, it has recently been added to the list of existing cryptominer malware.
Crypto-Miner Malware
In December of last year, Check Point Software Technologies has recorded a rise in the use of crypto-miners that has a similar modus operandi to Coinhive: Cryptoloot and Rocks. These cryptominers aren’t all that different to Coinhive in that they hijack the victim PC’s resources to be used for mining cryptocurrency. Coinhive is leading Check Point’s top ten list of most wanted malware, with Cryptoloot coming in at no. 3 and Rocks at no. 10. The blog post notes that the reason people are turning to cryptomining is because people started using Adblockers to block ads, thereby cutting these websites’ ad revenues.
Then just this month Texthelp’s Browsealoud script was hacked and turned into a cryptominer dispenser. Browsealoud was originally a script that adds speech that reads text on websites. This was made with people with Dyslexia in mind, as well as for people who are not that good reading in English. Browsealoud is used in a number of government sites, health sites, and education-related websites around the world. Then last 11th Texthelp was attacked by hackers and modified Browsealoud’s JavaScript file. Browsealoud would then execute and install a Coinhive cryptojacking script into the victim’s PC and make it mine cryptocurrency.
Soon, government websites from UK, the US and Australia were infecting PCs with cryptomining malware. As many as 4,275 sites were affected. Eventually, Testhelp had to shutdown Browsealoud to address the issue.
Switching Modus Operandi
One could only watch in amazement as hackers switch their modus operandi from hacking and threatening people to never announcing their attacks and silently mine cryptocurrency. And with the noticeable spike of incidents, it is very likely that this is just the beginning. Hackers will most likely devise more means to attack the users’ PCs to mine more cryptocurrency.