This Android Malware Hostages Your Device for a $300 Ransom. Will You Pay?
![By Intel Free Press [CC-BY-SA-2.0 (http://creativecommons.org/licenses/by-sa/2.0)], via Wikimedia Commons](https://techtheday.com/wp-content/uploads/2014/05/Android-Smartphone.jpg)
By Intel Free Press [CC-BY-SA-2.0 (http://creativecommons.org/licenses/by-sa/2.0)], via Wikimedia Commons
The malware in question is called “Android-Trojan.Koler.A” and it comes with a novel way of bothering its victims. It demands a $300 fine from the owner of the infected device for allegedly viewing, saving, or spreading prohibited pornography. The malware claims that the device will be eventually locked if the payment is not made as soon as possible.
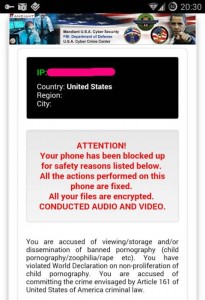
The screen displayed by the malware shows the device’s IP address, the country where the device is located, and empty fields for region and city.
The main texts shown are as follows:
ATTENTION!
Your phone has been blocked up for safety reasons listed below.
All the actions performed on this phone are fixed.
All your files are encrypted.
CONDUCTED AUDIO AND VIDEO.
You are accused of viewing/storage and/or dissemination of banned pornography (child pornography/zoophilia/rape etc.). You have violated World Declaration on non-proliferation of child pornography. You are accused of committing the crime envisaged by Article 161 of United States of America criminal law.
The malware even includes an excerpt of Article 161 of the United States criminal law.
Another Android Malware?
As the name itself implies, this malware is aimed at devices that run the Android operating system. According to Ars Technica, this recently discovered malware is obtained by viewing porn. It disables Android mobile devices until those infected pay the $300 indicated on the screen. This type of malware is also referred to as a ransomware.
To make things more intimidating, the malware even uses the logos of the FBI and the US Office of the President along with a photo of President Barack Obama himself in an accusing gesture. Also, in an attempt to make the threat more convincing, the malware also makes use of geolocation to identify (at least) the country where the infected device is located.
How Does It Manifest?
As mentioned earlier, the malware shows a persistent message about being “blocked up” unless the payment is made. The malware’s primary component is a window that appears on top of all other applications. You might be able to go to your home screen by pressing the Android Home button but the malware’s window returns after 5 seconds.
How Can It Be Removed?
It’s possible to uninstall the malware manually by dragging it to the uninstall control provided that you can get enough time to drag it for uninstallation. if you are still using Android Gingerbread, uninstalling it will be difficult.
Where Does This Malware Come From?
The exact source of this new threat to mobile device user is yet unknown. However, according to Ars Technica, it is automatically downloaded from certain porn sites as those who want to see porn try to download something from these pornographic sites. These could video players said to be necessary for premium access to porn content. For now, it only affects Android devices.
How Many Victims So Far?
As the malicious software came to public attention, the victim count was at 68. Forty of this figure are from the United Arab Emirates while 12 victims were in the UK, 6 in Germany, 5 in the United States, and the remainder traced to Poland and Italy. These numbers may sound small but these are just initial counts. The actual number of those who fell for the trick could be considerably bigger.
How to Defend Yourself from It?
Android-Trojan.Koler.A is obtained from porn sites. As a preventive measure, it is advisable to avoid porn sites or to limit your options to the established ones that don’t have any record of spreading viruses and other forms of malicious software. Also, the malware will only be able to install itself on an Android device if the device allows apps that are not from the Android market or Google Play store. As such, it is recommended not to allow non-market apps from getting installed. Android devices, generally, don’t permit third party APK (non-market) installations unless intentionally changed by the device owner through the Settings.
300$? How Are the Perpetrators Taking the Money?
Expectedly, the people behind this malware will not use credit cards, PayPal, and other easily traceable money transfer services in claiming their “ransom” or the $300 payment being sought. They use services such as uKash and Paysafecard to make it very difficult to know who received the “ransom.”
![By Berishafjolla (Own work) [CC-BY-SA-3.0 (http://creativecommons.org/licenses/by-sa/3.0)], via Wikimedia Commons](https://techtheday.com/wp-content/uploads/2014/05/malware.jpg)
By Berishafjolla (Own work) [CC-BY-SA-3.0 (http://creativecommons.org/licenses/by-sa/3.0)], via Wikimedia Commons
Attacks on the Android operating system are becoming more aggressive and “innovative.” There is a need to be more cautious about them and to install all the necessary software protection. Even smartphone hacking is also on the rise. Device users should realize how viruses, malware, and other threats are no longer limited to desktop or laptop computers. There is a need for enhanced protection and more caution even among mobile device users.