Warning! The WannaCry Ransomware Attack of May 2017
On May 12, computers in Southeast Asia, and then the rest of the world, came under attack by hackers using exploits and hacking tools leaked out recently. The attack was aimed to everyone. Government agencies or companies whose computers have been infected had their operations grind to a halt.
Holding your data for ransom
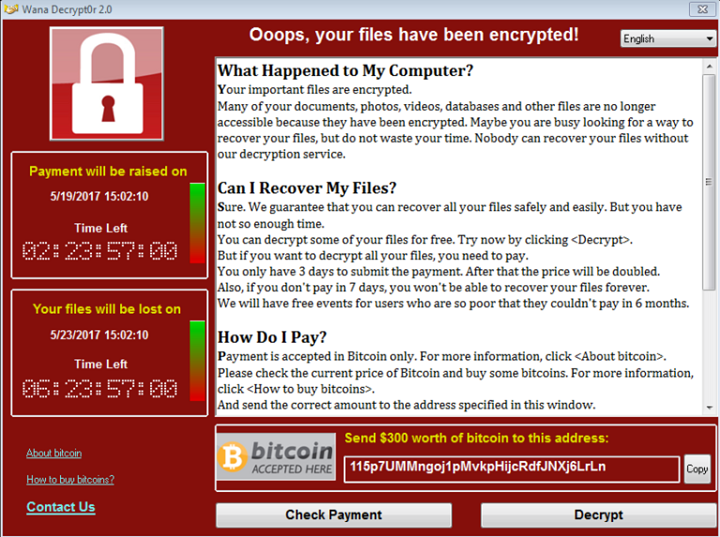
The method of attack was through the use of a ransomware, known as WannaCry, also known under the names WannaCrypt, WanaCrypt0r 2.0 and Wanna Decryptor. The idea was to hold your files on ransom by encrypting them, making them unusable. Then the hackers who had your files encrypted would ask you to pay up the ransom or you’ll never be able to unencrypt your files. Depending on the hackers, they may choose to encrypt some or all of your hard drive.
This type of electronic extortion attacks had its root to the AIDS Trojan by Joseph Popp way back in 1989. Since then, as computers and anti-virus companies got smarter, so does the crooks who created them, continuously adding more sophisticated features and seeking ways to infiltrate computers.
According to SophosLabs, unlike most ransomwares that arrived via email, WannaCry’s attack starts with a network worm attack. A worm is a malware that replicates itself to spread to other computers. In this attack the worm spreads out over the Internet, attacking any computer that isn’t up-to-date with its patches, particularly the one Microsoft released last March to fix a dangerous exploit known as Eternal Blue. Eternal Blue is believed to have been discovered, developed and kept secret by the US National Security Agency. The information was all leaked by the hacker group Shadow Brokers on April 14 this year.
After the worm gains access to your computer, it then installs DoublePulsar. DoublePulsar is another hacking tool said to be developed by the US NSA and leaked by the Shadow Brokers alongside Eternal Blue’s information. Once installed, DoublePulsar can be commanded to execute the malware’s payload.
Once the payload is executed, it then encrypts your files, deletes your backup and installs the executable that displays the ransom note. On the WannaCry note it explains to the victim what happened and how much they need to pay to get their files back. They also tell the user to pay using Bitcoin, a virtual currency that provides anonymity. They also threaten that if the victim does not pay on time, the ransom will be doubled.
The Victims
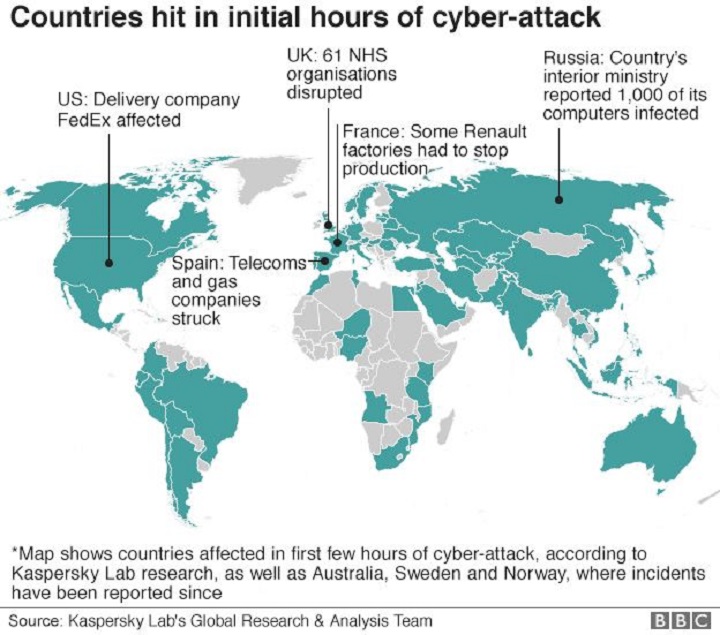
According to a recent report by BBC, most computers that got infected were running Windows 7 and other computers that didn’t update the March patch mentioned earlier. What’s appalling is that many of these computers are used by companies likeFedEx and government agencies like the UK’s National Health Service organizations and hospitals were hit as well, causing them to turn away patients. Russia reported 1,000 computers infected. Spain’s telecommunication and gas companies were affected too.
The attack, which spread out from Asia onto the rest of the world in a single day, has infected more than 200,000 computers.
How it was stopped
Marcus Hutchins, a.k.a. MalwareTech, a whitehat hacker, was the first to find the kill switch for the spread and activation of the ransomware. The ransomware apparently checks a webdomain to see if it can access it or not. If it can, the malware will go dormant. If it can’t it will activate. All he did was have the web domain registered and this stopped the spread globally.
The Aftermath
Following Marcus’ discovery, hackers have turned to the Mirai botnet to execute a DDoS attack on the webdomain to knock it offline so they can reignite the malware’s impeded attack. Marcus believes that this is a different group who just wants to see it all start again for amusement.
On May 21, EternalRocks was discovered by a Croatian security expert, Miroslav Stampar. The new malware also employs several of the NSA hacking tools leaked by the Shadow Brokers group.
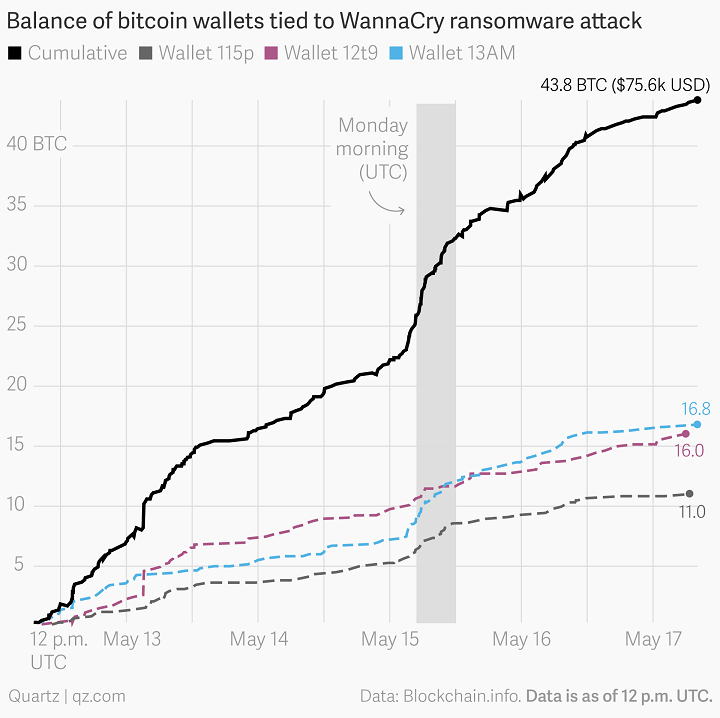
All in all, the hackers got away with only less than $100,000 from those who paid the ransom. The group is suspected to have links to North Korea.