Your Smart LED Lights Could Be Leaking Your Wi-Fi Password
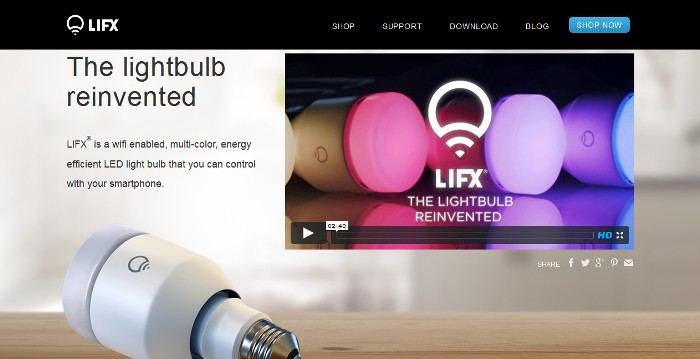
You would want to install smart LED lights for your homes for greater convenience and connectivity. But what if these smart lights are overly enthusiastic in keeping you connected? What if they unwittingly let your neighbors and strangers access your network by sharing your Wi-Fi password?
The Hacking
Context Information Security research director Michael Jordon explained the process they did to obtain the Wi-Fi username and password of the household that used a LIFX light bulb. He said it was basically about exploiting the flaw in the way the bulbs communicate with each other. Smart lighting like LIFX have Wi-Fi connectivity so they can be accessed via Wi-Fi connection. What the team did was to pose as one of the LIFX bulbs that tries to join the network of LIFX bulbs in a home.
LIFX smart light bulbs form a network by having a master bulb that receives commands from a smartphone app developed to control it. The master bulb receives commands from the smartphone or mobile device and broadcasts the signal to the rest of the bulbs in the wireless mesh network.
It took two weeks for the experts at Context Information Security to finally crack the system but they only needed to use cheap and readily available equipment.
Technical Details
Context Information Security presented details about the hacking in a post entitled “Hacking into Internet Connected Light Bulbs.” Here’s a summary of how they did it:
LIFX light bulbs employ new new wireless network protocols that Context Information Security researchers found intriguing, in addition to their observation that the LIFX mesh network protocol was considerably unencrypted. These protocols work on the 802.15.4 6 LoWPAN wireless mesh network, a wireless communication specification built upon IEE 802.15.4, which is used by Zigbee to enable the forwarding of IPv6 packets over low power personal area networks (PAN). To pose as one of the bulbs, the researchers used a device that also works with the 802.15.4 specification, the ATMEL AVR RAven with Contiki firmware in particular.
The researchers dissected the LIFX mesh network protocol to extract messages related to the control of the bulbs. They monitored the data packets when a new bulb was added. Since the master bulb also transmits messages that contain Wi-Fi details, the researchers were able to extract the username and password. The researchers noted how the LIFX system was somewhat lax in the handling of Wi-Fi credential transmissions. The details were encrypted but the researchers were able to decrypt them by examining the microcontrollers from the LIFX lighting system.
Cropped screenshot of Context Information System’s blog on the smart light vulnerability (http://www.contextis.com/blog/hacking-internet-connected-light-bulbs/)
LIFX Response
LIFX created the LIFX smart light light bulb through a Kickstarter campaign. It has since become one of the leading brands when it comes to smart lighting, offering a product touted as the “light bulb reinvented.“ It managed to obtain funding that was 13 times higher than the target amount. Also, it now has more than 9,000 backers.
Upon learning about this vulnerability, the maker of the LIFX bulb promptly provided a fix via firmware update. In a post on its official blog, the company admitted that “there was a potential security issue regarding the distribution of network configuration details on the mesh radio but no LIFX users have been affected that we are aware of.” The company then proceeded to call for users to upgrade their firmware, saying “As always we recommend that all users stay up-to-date with the latest firmware and app updates.” To emphasize, updating is necessary for both the bulbs’ firmware and the app used to control the bulbs, regardless of operating system.
It’s important to point out, though, that being a firmware upgrade, the owner of the smart bulbs need to allow the upgrading of the firmware. The bulbs don’t upgrade by themselves and not many may be able to pay attention to this call for an upgrade.
Firmware Upgrading for All “Internet of Things” Products
While the vulnerability has not been pointed out in other similar smart bulbs and appliances yet, it is recommended to upgrade to the latest firmware as soon it becomes available. This news most likely will have alarmed other smart lighting and appliance manufacturers to examine their own wireless connection protocols and implement the firmware fixes necessary to ensure network security.